使用 CA 根证书签 SAN SSL 证书
简介
在 自签名 SSL 证书 中可以简单的得到 ssl 的证书。
如果我们有多个端点需要部署,那么就可以先创建 CA 根证书,部署根证书到服务器,并且客户端信任该根证书,那么使用该根证书签发的域名证书都会被信任,就不需要每一个域名再去设置信任规则了。
比起简单创建 ssl 证书,我们只需要先创建 CA 根证书,再创建 ssl 证书即可。只是参数有少许变化。
创建 CA 根证书
创建 CA 证书使用命令
1 | openssl req -x509 -newkey rsa:4096 -sha256 -days 3650 -nodes -keyout ca.key -out ca.crt |
根据提示输入相应的信息
1 | ..+.....................+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.+...+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*..........+..............+.........+...+.......+...........+.......+.....+.......+...+.....+.......+.................+......+....+.....+....+..+....+...+.....+.......+...+..+.........+......+.+............+............+.........+.....+.......+..+...+.......+............+.........+.....+....+..+.........+.......+..+...............+................+.....+....+...............+............+...+...+.........+..............+............+.........+......+...+..........+...........+...+.+...............+.................+.........+.+.................+.+.....+......+.+..+.......+.....+.+........................+...+..+....+..+...+..........+..+.............+.....+..........+...........+......+......................+..+.............+.....+...+...+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ |
我们发现和创建简单 ssl 证书并没有什么区别,只是在 Common Name
一项中填写根证书的名称,我这里填写的是 JackVip RSA SSL CA。然后 CA 证书就创建好了。
使用 CA 根证书签发服务器证书
使用以下命令创建服务证书
1 | openssl req -newkey rsa:4096 -x509 -sha256 \ |
这里新增加了 3 个参数
-CA需要指定 CA 证书的路径-CAkey指定 CA 证书的秘钥-addext用来指定SAN(subjectAltName)信息,如果不设置这一项,就算信任了 CA
证书,浏览器也会提示网站证书不合法。一般会提示安全证书没有指定主题备用名称
按照提示输入信息
1 | .+...+....+.....+...+....+...+...........+.+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*..+.+..+............+...+................+............+..............+...+.+..+.......+...+.....+...+......+......+...+.........+.+..+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.+...+.....+.............+.........+...+..+..........+.................+......+.......+...+........+.......+.....+........................+.....................+...+...............+......+...+...+....+...+...+..+......+.......+...+.....................+........+.+.....+....+.....+.......+...+............+......+..+...+....+...........+...+.+.....+.............+...+..+...............+...+...................+.........+......+.....+.+.....+..........+..+............+.+........+....+......+...........+.........................+....................+.+...+.....+.+........+.......+......+........+....+...+.....+....+...........+............+...............+.............+..............+.+..+..........+...........+...................+..+.............+...+.................+............+.+............+...........+.+.....+...............+.+...+......+...+..+...+...+...+.+...........+..................+..........+..+............+............+.+...................................+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ |
配置 CA 证书和服务器证书到 nginx
添加虚拟机配置到 nginx
1 | server { |
客户端信任 CA 证书
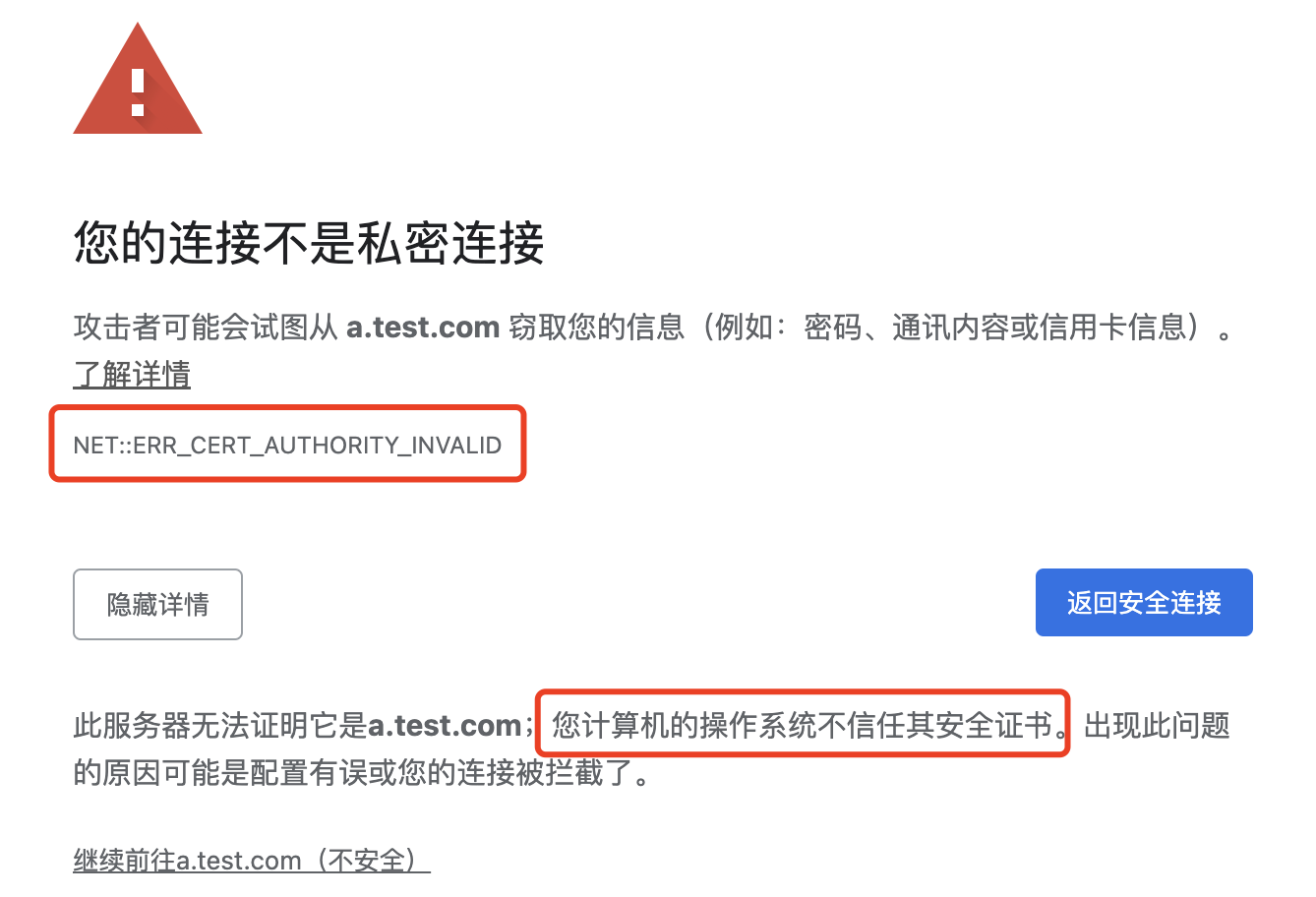
完成上述配置,我们直接用浏览器打开 https://a.test.com:8443
会提示 您计算机的操作系统不信任其安全证书
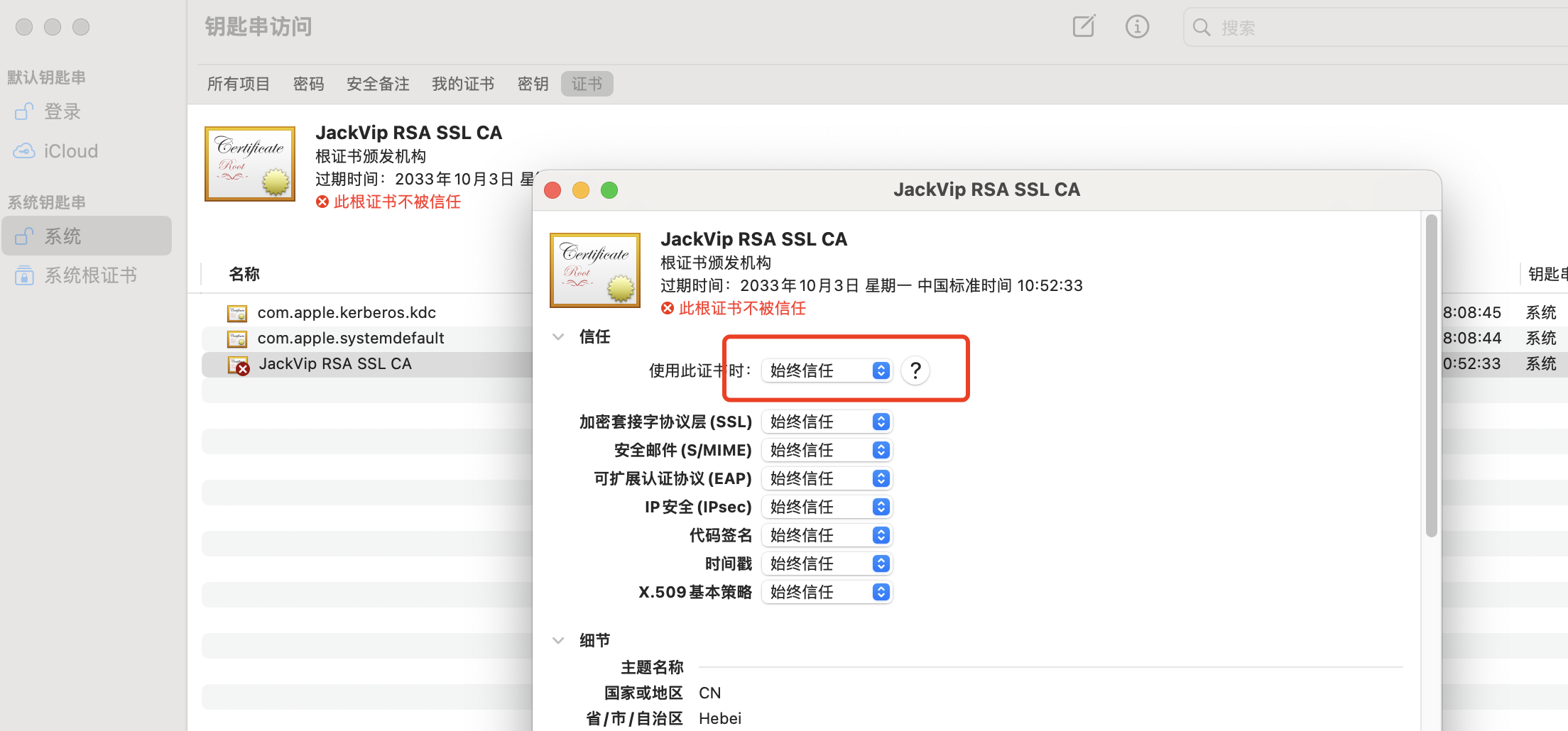
我们把 ca.crt 下载到客户电脑端,双击打开导入到钥匙串(不同系统可能会不同),并设置成始终信任。
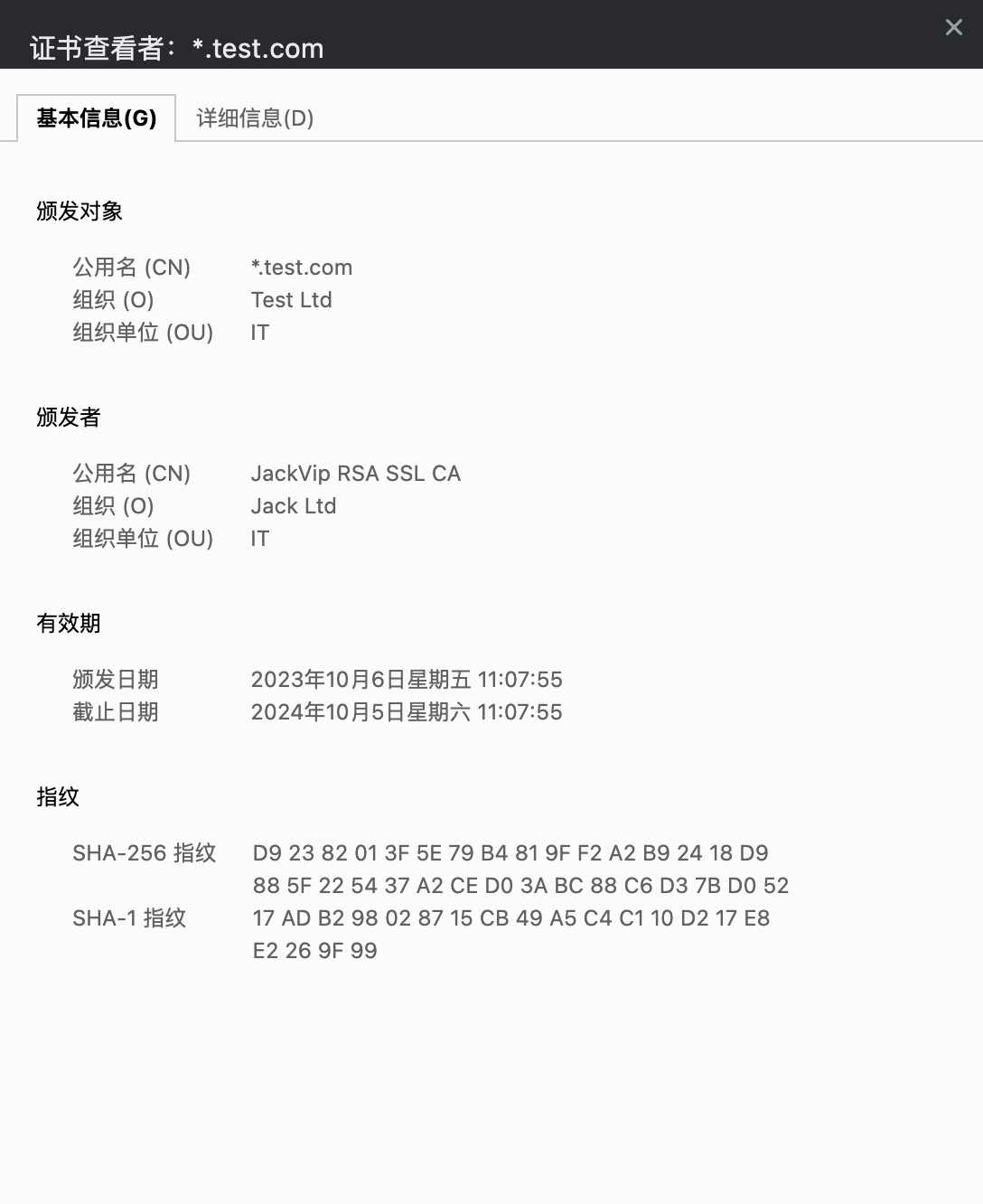
再次访问网址(最好重新打开无痕模式进行访问)就可以看到证书已经正常了,颁发者和颁发对象信息都是正确的。
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Jack.vip!